Encryption Configuration¶
SwiftStack supports the optional encryption of object data at rest on storage nodes. The encryption of object data is intended to mitigate the risk of users’ data being read if an unauthorised party were to gain physical access to a disk.
Plan for Encryption¶
To ensure all potentially sensitive user data is protected the Encryption feature is enabled Cluster wide. You should enable encryption before you deploy on new hardware to ensure that all user data committed to disk is protected.
Note
Currently, you may only enable the Encryption feature before the initial deployment of the cluster. If you are interested in using encryption on an existing SwiftStack cluster, please contact support.
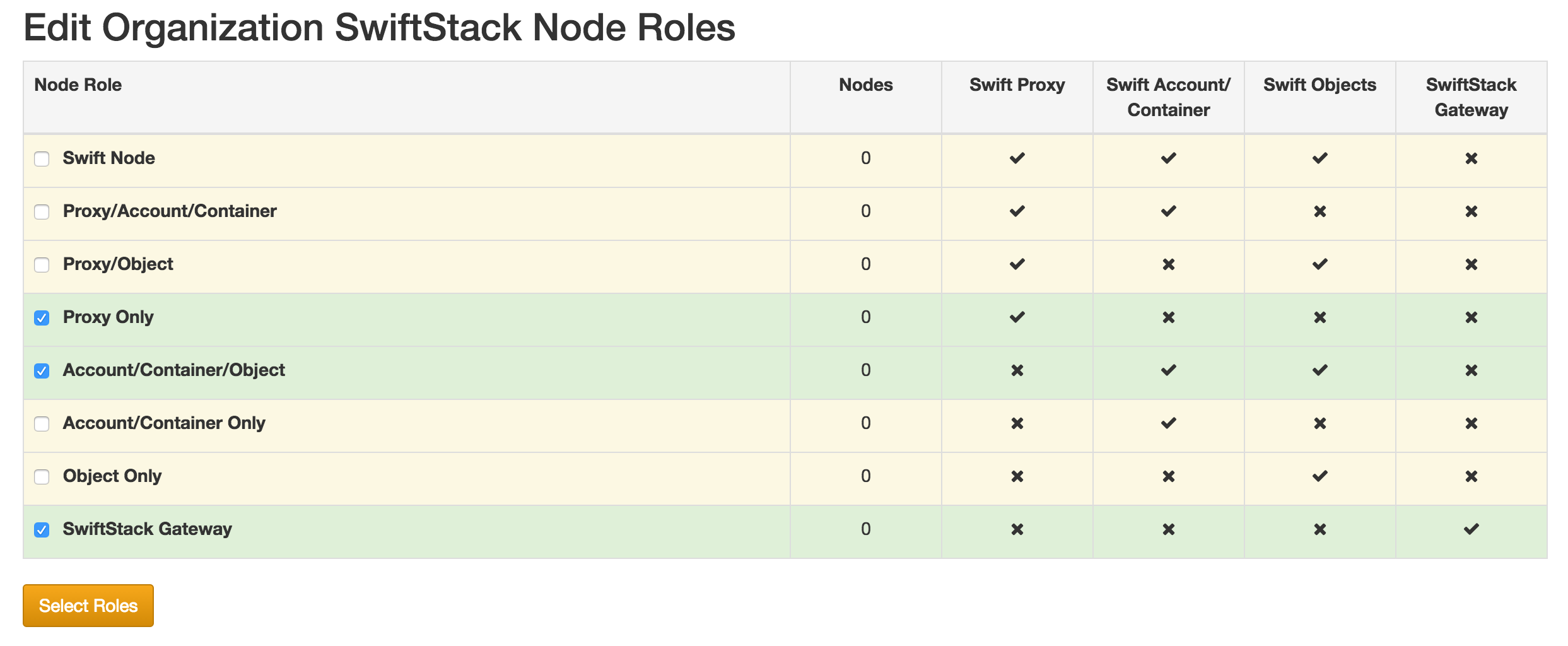
Configure Roles¶
Optimal threat isolation requires you to segregate your access tier from your storage tier. Encrypted data is never stored in the access tier. No unencrypted key material is ever written into the storage tier.
Navigate to the Cluster Node Roles under the Organization tab.
Enable the Proxy Only Role.
You must also enable one or more of the storage only roles, Account/Container/Object, Account/Container Only, or Object Only
Avoid using roles that combine the Proxy service with Account/Container or Object services by disabling the All Swift Services role.
Build Cluster¶
All the steps to Configuring Your Cluster and Provisioning Your Node are preformed like normal, but before Deploying Changes to the Cluster you should stop to enable Encryption!
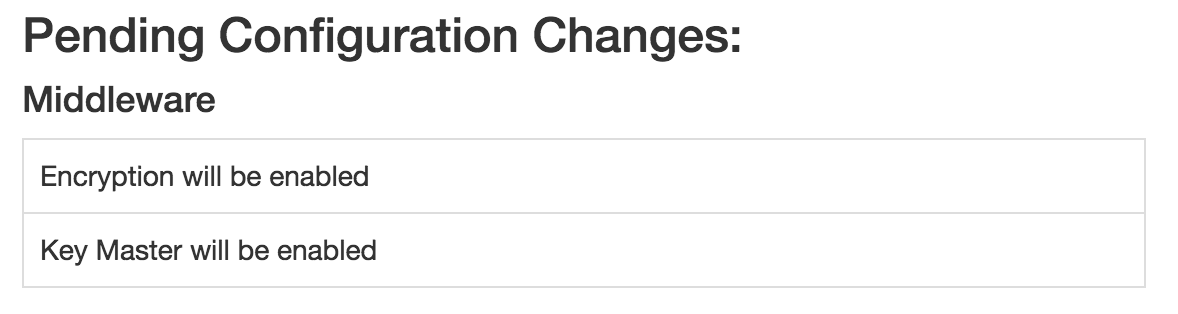
Enable Encryption¶
Encryption is enabled via Object API Features and Middleware.
- Enable the Encryption Middleware
- Enable the Keymaster Middleware or KMIP Keymaster Middleware
Deploy Cluster¶
You may now proceed Deploying Changes to the Cluster
You should confirm that both the Encryption Middleware and Keymaster Middleware will be enabled before you deploy.